AI
our blog
10 Critical IoT Vulnerabilities Every CTO Must Address

Overview
The article delineates ten critical IoT vulnerabilities that Chief Technology Officers (CTOs) must confront to bolster security in IoT environments. It underscores the necessity of implementing robust security practices—such as:
- Strong password policies
- Secure update mechanisms
- Effective device management strategies
to mitigate risks and safeguard against potential cyber threats linked to these vulnerabilities. By addressing these vulnerabilities, CTOs can enhance their organization's security posture and foster a more resilient IoT ecosystem.
Introduction
The Internet of Things (IoT) is revolutionizing the way devices connect and communicate. However, this technological advancement introduces a plethora of security vulnerabilities that can jeopardize sensitive data and operational integrity. For Chief Technology Officers (CTOs), understanding and addressing these vulnerabilities is not merely a technical necessity; it is a strategic imperative that can protect their organizations from potential cyber threats. What are the critical vulnerabilities that demand immediate attention? How can organizations effectively mitigate these risks to cultivate a secure IoT ecosystem? This article explores ten essential IoT vulnerabilities every CTO must confront, providing insights and actionable strategies to enhance security and resilience in an increasingly interconnected world.
Studio Graphene: Comprehensive Solutions for IoT Security Vulnerabilities
Studio Graphene establishes a robust framework for tackling IoT vulnerabilities through its innovative digital solutions. By leveraging AI and emerging technologies, the agency effectively identifies and mitigates IoT vulnerabilities associated with IoT devices. Their cooperative approach ensures that protective measures—including comprehensive information protection assessments, regulatory reviews, and proactive compliance management—are seamlessly integrated into the product development lifecycle. This unwavering commitment to quality assurance and capacity planning not only enhances deployment efficiency but also equips clients with substantial protection against potential threats.
For businesses eager to harness the power of IoT while safeguarding their operations and data integrity, adopting a proactive security strategy that encompasses regular compliance assessments and updates is imperative.
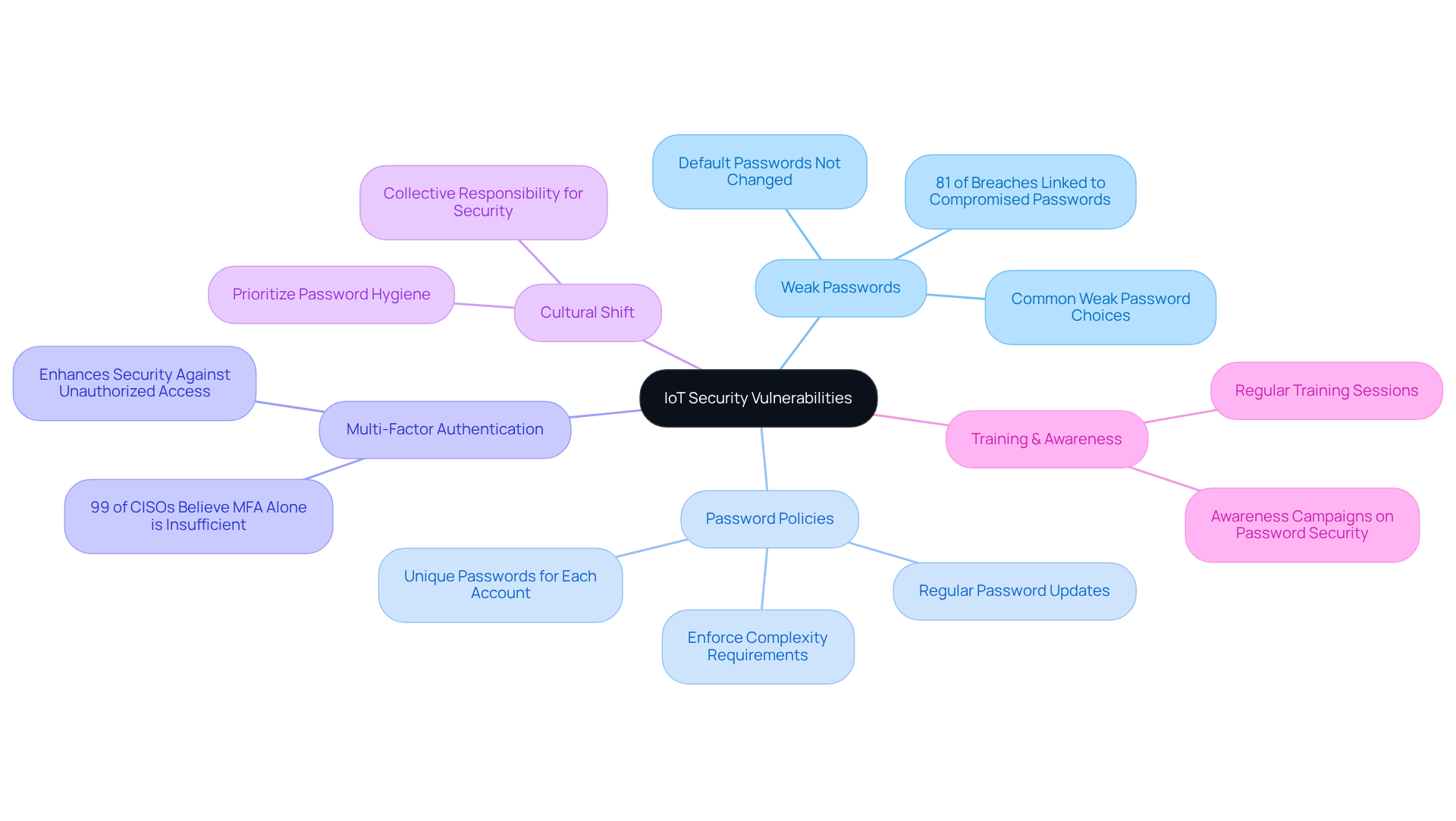
Poor Passwords: A Major IoT Security Vulnerability
A significant IoT vulnerability in IoT systems stems from the widespread use of weak passwords. Many devices are shipped with easily guessable default passwords, and users often overlook the necessity of changing them. To address this critical issue, CTOs must implement robust password policies that enforce complexity requirements and regular updates. Organizations should advocate for the use of long, unique passwords and educate users about the importance of avoiding common pitfalls, such as reusing passwords across different platforms.
Studies indicate that 81 percent of breaches are linked to compromised passwords, which underscores the need for strong password practices to address IoT vulnerabilities. The implementation of multi-factor authentication (MFA) can further enhance security by adding an extra layer of protection against unauthorized access. However, a staggering 99 percent of Chief Information Security Officers (CISOs) believe that MFA alone is insufficient, highlighting the need for comprehensive protection strategies that incorporate strong password practices.
Experts advocate for a cultural shift towards prioritizing password hygiene, emphasizing that safety is a collective responsibility. Joseph Carson notes that "effective incident response depends on two elements: information and organization," which underscores the importance of organized protective measures alongside password policies. By cultivating an environment where employees grasp the significance of secure password management, organizations can significantly mitigate the risk of breaches. Regular training sessions and awareness campaigns can reinforce these practices, ensuring that all stakeholders are equipped to safeguard sensitive information effectively.
Adopting these best practices not only bolsters the security of IoT systems but also mitigates IoT vulnerabilities, contributing to a more resilient organizational structure against emerging cyber threats.
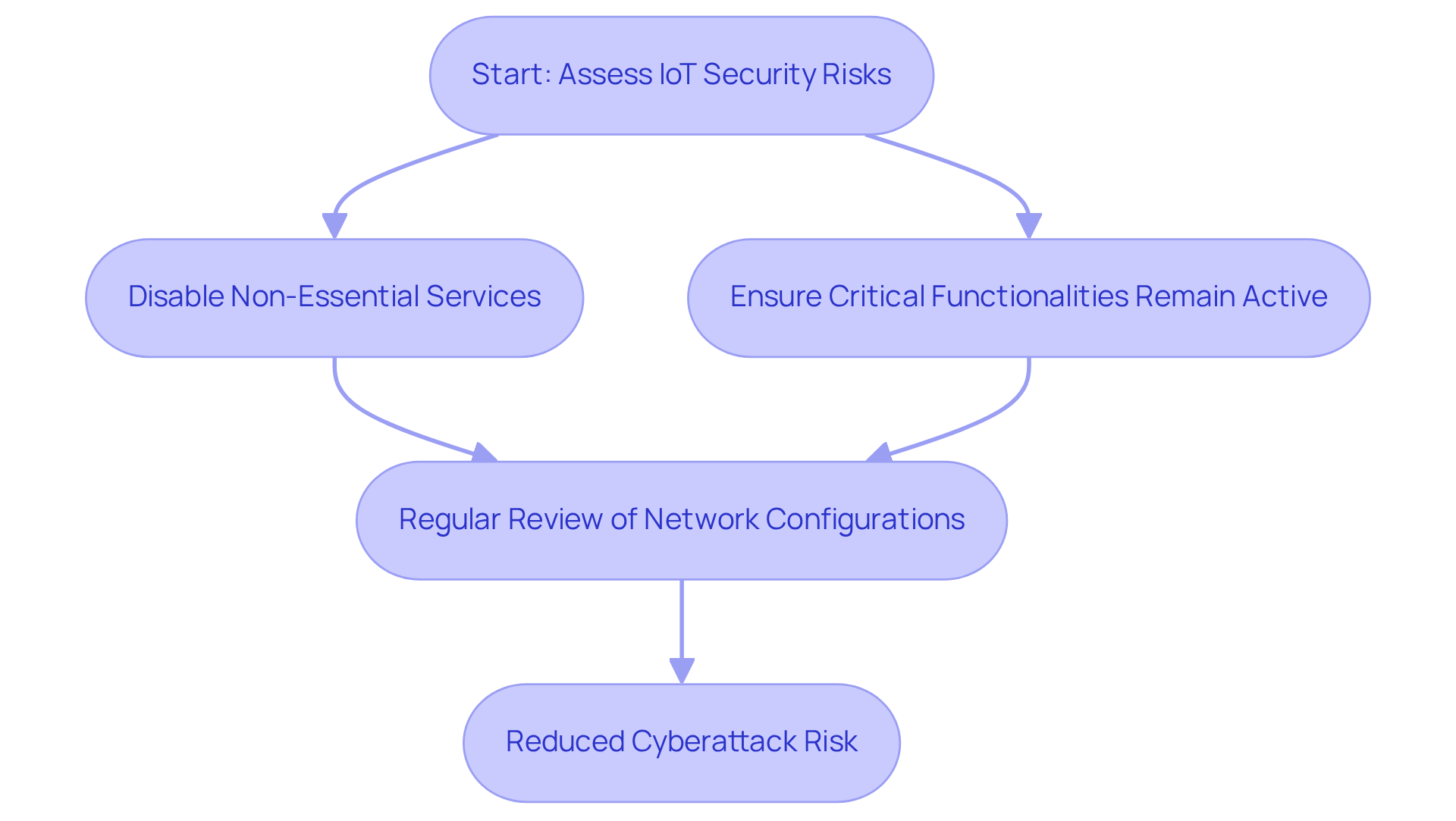
Unneeded or Insecure Network Services: Risks in IoT Security
Numerous IoT items come equipped with pre-installed network services that may not be essential for their core functions. These unnecessary services can serve as additional entry points for cyber attackers, significantly increasing the risk of breaches. In fact, Kaspersky reported 1.5 billion IoT vulnerabilities-related cyberattacks in the first half of 2021, highlighting the urgency of addressing these vulnerabilities.
To mitigate these risks, CTOs should implement rigorous audits of their IoT devices, focusing on:
- Disabling any non-essential services
- Ensuring that only critical functionalities remain active
Regular reviews of network configurations are vital for maintaining a secure environment. As cybersecurity specialist Bruce Schneier observes, depending exclusively on technology for protection is a misconception; a proactive method that involves auditing and deactivating unnecessary services is crucial.
Furthermore, since 60% of IoT vulnerabilities originate from unpatched firmware and outdated software, these audits are essential for improving protection. By taking these steps, organizations can significantly reduce the likelihood of successful cyberattacks.
Insecure Ecosystem Interfaces: A Critical IoT Vulnerability
Vulnerable ecosystem interfaces, particularly APIs and web interfaces, contribute to significant IoT vulnerabilities that threaten IoT safety. These interfaces often serve as entry points for attackers due to IoT vulnerabilities if not adequately secured. To mitigate these risks, CTOs must prioritize the adoption of secure coding practices, which encompass rigorous input validation and robust authentication mechanisms. Implementing these practices not only fortifies the interfaces but also substantially diminishes the likelihood of exploitation.
Routine testing and vulnerability evaluations are critical components of a proactive defense strategy. These measures assist in identifying and addressing potential weaknesses before they can be exploited. As Joseph Carson emphasizes, conducting comprehensive risk evaluations of IoT equipment is essential for understanding the protection environment and addressing IoT vulnerabilities to execute effective measures. Furthermore, with ransomware attacks projected to cost the world over $40 billion in 2024, the financial implications of insecure APIs cannot be overlooked. By fostering a culture of awareness and integrating safe coding practices into the development lifecycle, organizations can bolster their resilience against the evolving threat landscape posed by IoT vulnerabilities.

Lack of Secure Update Mechanism: A Vulnerability in IoT Devices
The lack of secure update mechanisms significantly exposes IoT technology to IoT vulnerabilities and increases the risk of cyber threats. Kaspersky reports an alarming 1.5 billion IoT cyberattacks in just the first half of 2021, underscoring the urgency for timely and secure updates. CTOs must prioritize implementing robust update processes that incorporate encryption and authentication to safeguard against known IoT vulnerabilities.
- One-click deployment and rollback capabilities through DevOps automation can streamline the update process, ensuring efficient deployment of new versions while allowing for quick reversion if issues arise.
- Furthermore, establishing effective communication pathways with users regarding the essential nature of these updates can enhance overall protection.
- As industry leaders emphasize, adopting strong encryption standards and adhering to Zero Trust principles are vital for ensuring the integrity of IoT solutions.
- Firms that have successfully improved their IoT protection through prompt updates illustrate the efficacy of these tactics, highlighting the necessity for a proactive approach to managing IoT vulnerabilities.
- In addition, incorporating continuous integration practices within DevOps can further enhance code quality and safety.
- Automated notifications within DevOps frameworks enable prompt action during incidents, further safeguarding IoT systems from potential threats.
- To bolster your IoT protection stance, consider establishing a regular update timetable and ensuring all stakeholders are aware of their significance.

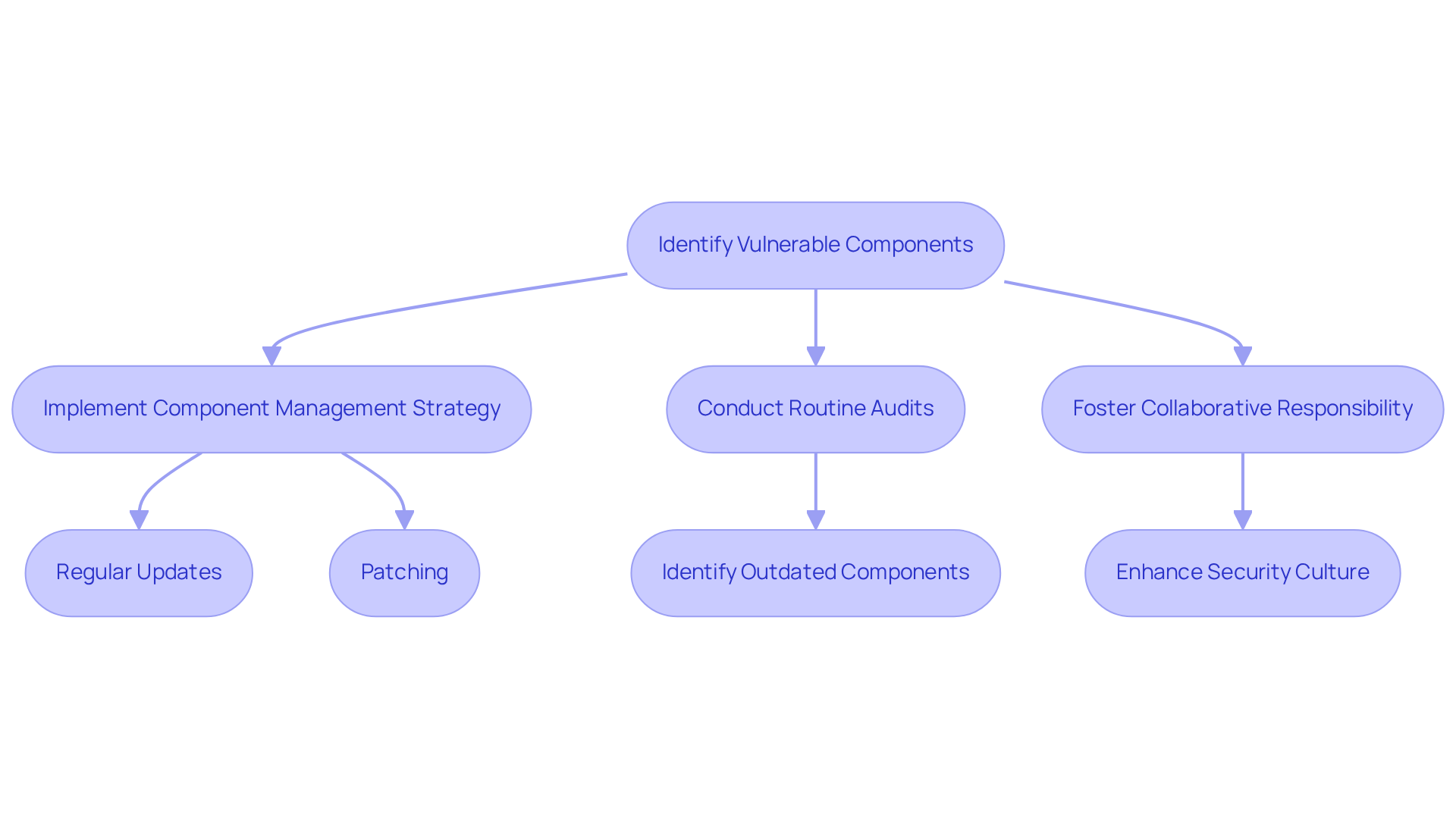
Insecure or Outdated Components: A Threat to IoT Security
The employment of vulnerable or obsolete elements in IoT devices contributes to significant IoT vulnerabilities that pose a risk to safety. Industry leaders have underscored that reliance on such components can create IoT vulnerabilities that cybercriminals can easily exploit. For example, an analysis revealed that the average open-source component in firmware is over five years old, highlighting the urgent need to address outdated components.
To mitigate these risks, CTOs must implement a comprehensive component management strategy that encompasses regular updates and patches for all hardware and software elements. This proactive approach not only addresses current vulnerabilities but also fortifies the organization’s overall protective posture.
Conducting routine audits of the technology stack is crucial for identifying outdated components that need replacement or upgrading. Companies like Forescout have demonstrated the effectiveness of component audits in enhancing IoT security, revealing an average of 161 known IoT vulnerabilities per firmware image. This underscores the imperative for organizations to prioritize component management, significantly reducing their exposure to cyber threats and ensuring a more resilient IoT infrastructure.
Furthermore, as John Gallagher emphasizes, securing IoT systems is a collective responsibility within organizations, reinforcing the necessity for collaborative efforts in cybersecurity.
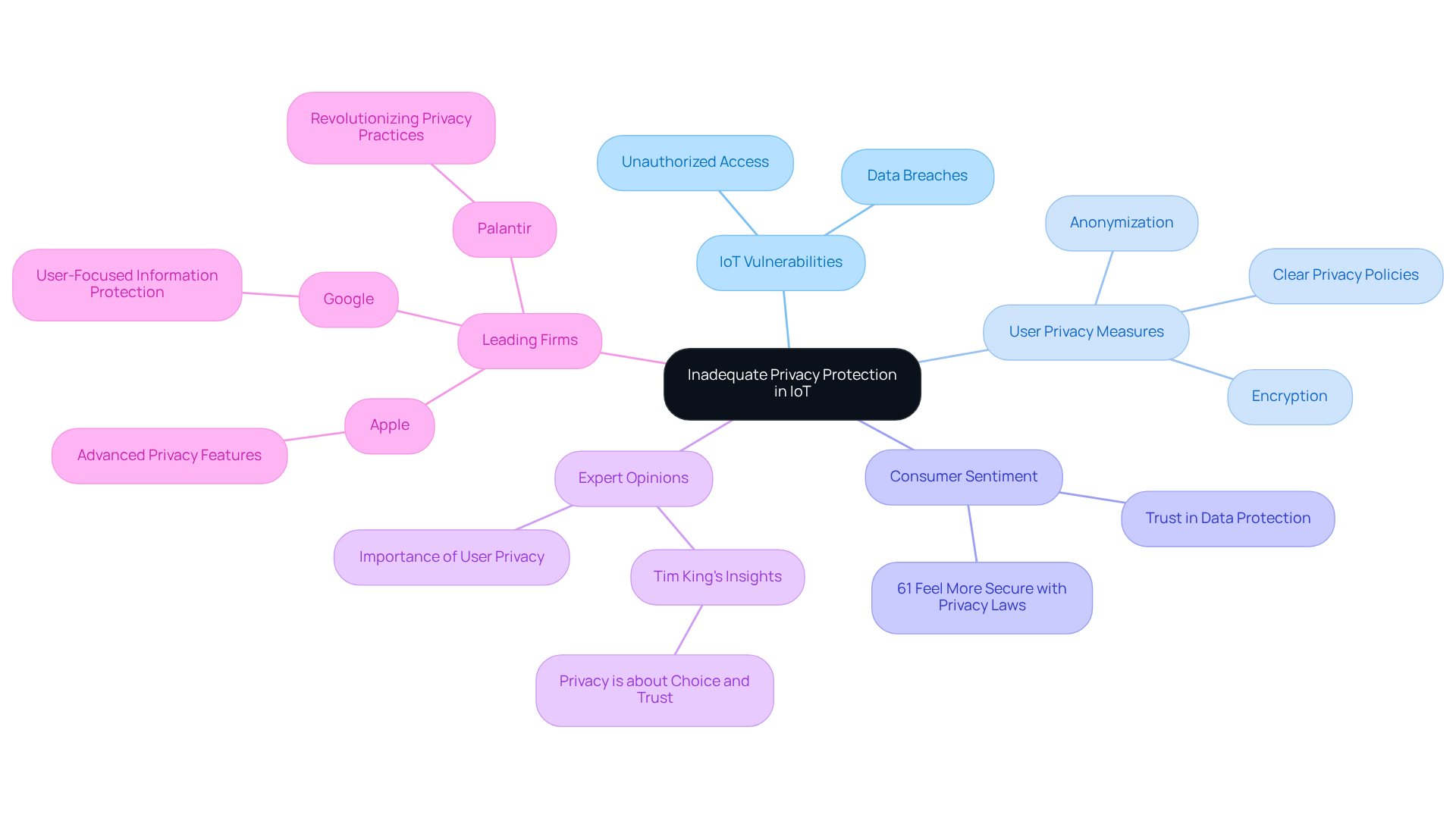
Inadequate Privacy Protection: An IoT Security Concern
Insufficient privacy safeguards in IoT devices create IoT vulnerabilities that present significant threats, including unauthorized access to information and data breaches. To address these IoT vulnerabilities, CTOs must prioritize user privacy by implementing robust protection measures such as encryption and anonymization of sensitive information.
Establishing clear privacy policies and ensuring compliance with evolving regulations are essential steps to build user trust and mitigate potential risks. Recent findings indicate that 61 percent of global consumers feel more secure when privacy laws are enacted to protect consumer information, underscoring the critical need for effective protection.
Experts emphasize that robust information protection not only secures user details but also enhances overall trust in IoT solutions by mitigating IoT vulnerabilities. Tim King, Executive Editor, asserts that 'Privacy is fundamentally about choice, trust, and providing customers control over how their information is handled.'
Leading firms like Apple and Google are at the forefront by incorporating advanced privacy features into their IoT devices, demonstrating a commitment to user-focused information protection. Furthermore, technologies such as Palantir are revolutionizing information privacy practices, showcasing how organizations can effectively enhance user privacy.
By adopting these measures and conducting regular security audits, organizations can cultivate a secure environment that mitigates IoT vulnerabilities while respecting user privacy and leveraging the benefits of IoT technology.
Unsecured Data Transfer and Storage: A Vulnerability in IoT
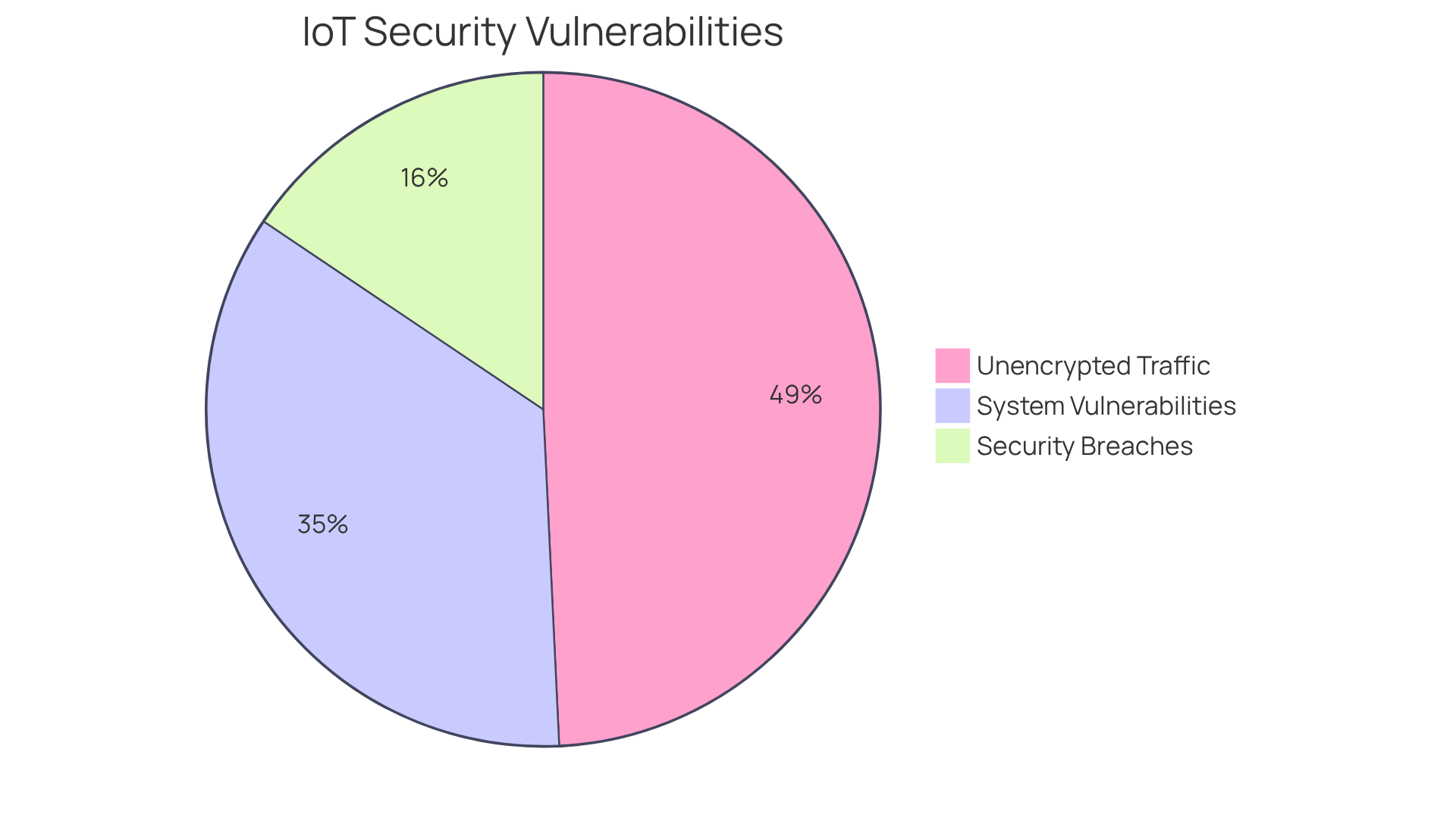
Unsecured information transfer and storage present significant IoT vulnerabilities, exposing sensitive details to potential breaches. To mitigate these risks, CTOs must implement robust encryption protocols for information both in transit and at rest. Protocols such as TLS (Transport Layer Security) and AES (Advanced Encryption Standard) are essential for safeguarding information integrity and confidentiality.
Alarmingly, 98% of IoT equipment traffic remains unencrypted, rendering it susceptible to interception and theft. Furthermore, 31% of organizations reported experiencing a security breach this year, underscoring the real-world consequences of unprotected IoT information. Additionally, 70% of IoT systems exhibit considerable IoT vulnerabilities due to inadequate coding and the absence of encryption, highlighting the pressing need for strong encryption measures.
Employing secure storage solutions, including encrypted databases and secure key management practices, is vital for protecting sensitive information from unauthorized access. Regularly examining access controls and ensuring compliance with industry standards can further bolster protective measures. Ongoing oversight of IoT equipment is also crucial, as encryption forms part of a broader protection strategy.
As cybersecurity expert Ginni Rometty aptly stated, 'Cybersecurity is more than a technology issue; it is a business issue.' By prioritizing encryption and secure data practices, organizations can significantly reduce their exposure to cyber threats and uphold the integrity of their IoT ecosystems.
Lack of Device Management: A Key IoT Security Vulnerability
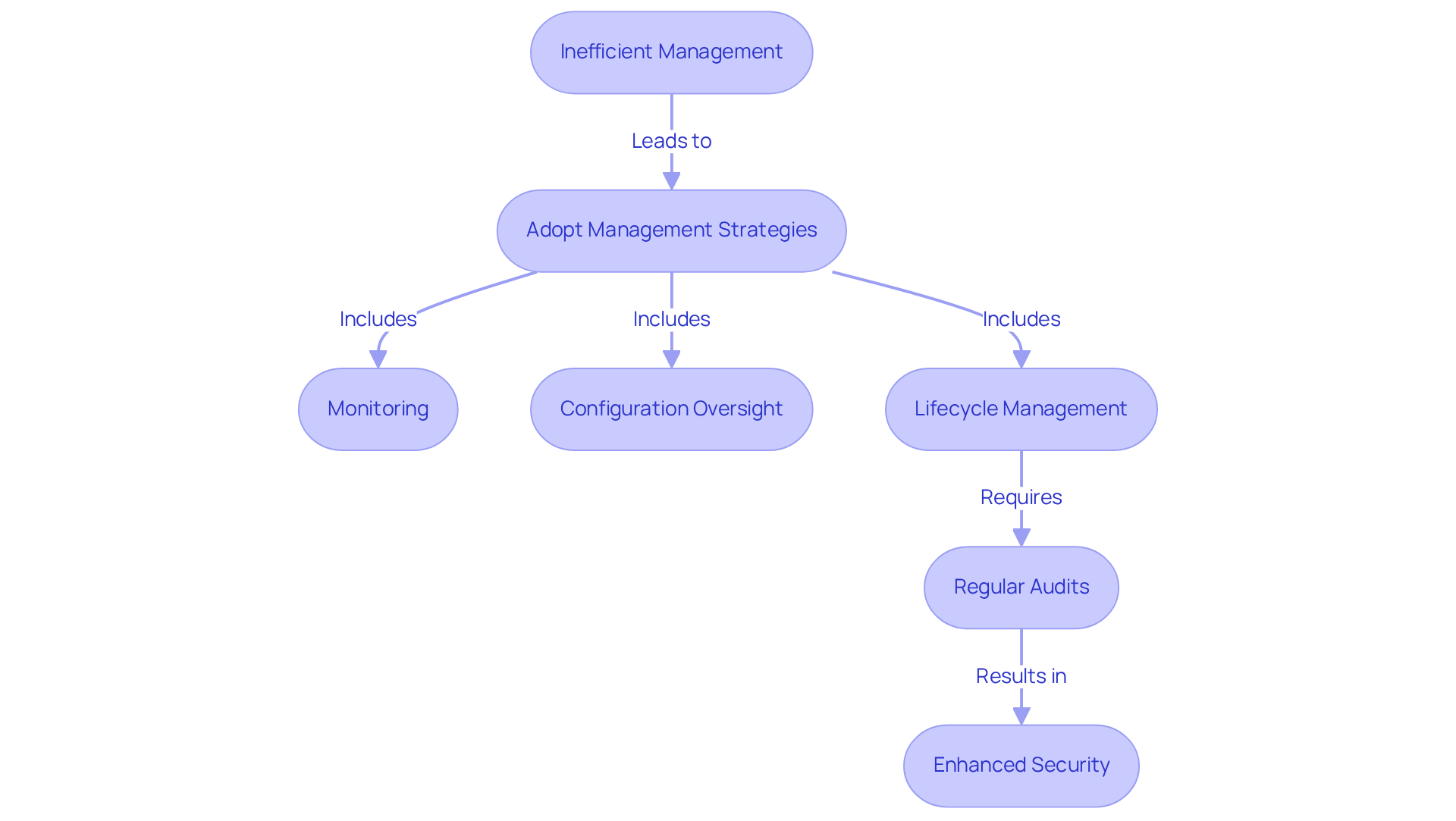
Inefficient management of equipment significantly exposes IoT deployments to IoT vulnerabilities. To combat this challenge, CTOs must adopt comprehensive management strategies that encompass monitoring, configuration oversight, and lifecycle management. Regular audits of equipment inventories are essential to ensure all items are accounted for, aiding in the recognition and addressing of potential risks.
For instance, firms that have effectively strengthened their IoT protection through lifecycle management have reported enhanced operational efficiency and proactive issue resolution. Bridgera Monitoring exemplifies a tailored solution that enables real-time monitoring of critical parameters such as particle density, pressure, humidity, temperature, and Air Changes per Hour (ACH). This capability not only facilitates immediate alerts for swift responses but also fosters informed decision-making through advanced analytics and tailored reporting.
The influence of efficient equipment management on IoT vulnerabilities and overall security cannot be overstated. It guarantees that IoT vulnerabilities are recognized and addressed throughout the lifecycle of the system, ultimately contributing to a safer operational environment. Bridgera stresses that upholding high air quality standards is essential in vital environments such as healthcare facilities and construction zones, underscoring the significance of strong equipment management practices. Industry leaders consistently emphasize that effective management of equipment is crucial for protecting IoT ecosystems from IoT vulnerabilities.
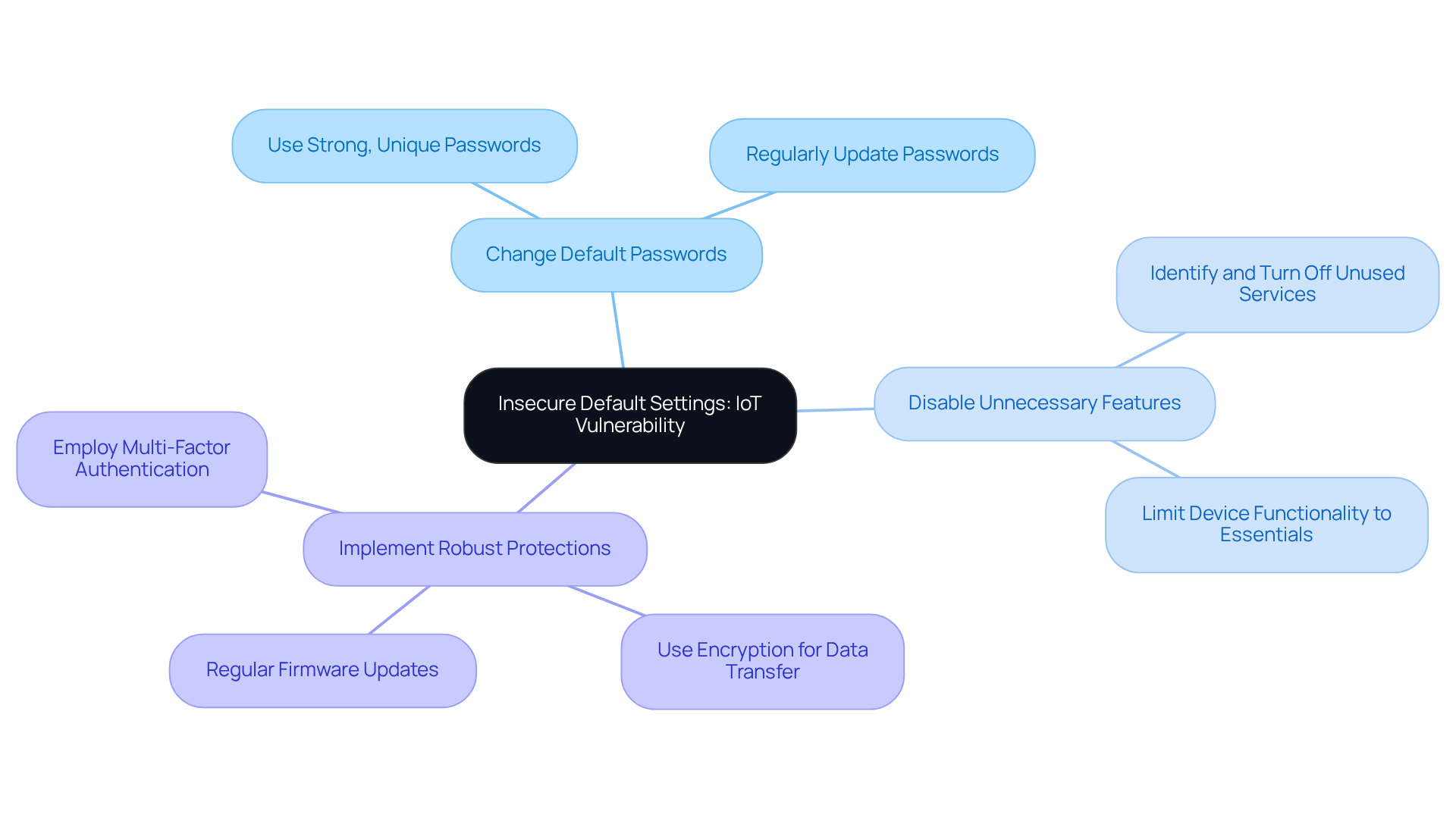
Insecure Default Settings: A Common IoT Vulnerability
Insecure default configurations in IoT gadgets create significant IoT vulnerabilities that cybercriminals can easily exploit. To mitigate this risk, CTOs must prioritize secure configurations prior to deployment. This includes:
- Altering default passwords
- Disabling unnecessary features
- Ensuring that devices are equipped with robust protective measures from the outset
Companies like Armis and AWS have underscored the importance of these practices, offering resources and guidelines to assist organizations in effectively securing their IoT environments. Furthermore, educating users about the necessity of changing default settings is crucial; studies indicate that informed users are more likely to adopt secure practices, significantly diminishing the risk of unauthorized access. By cultivating a culture of security awareness and implementing stringent configuration protocols, organizations can fortify their defenses against potential threats, particularly IoT vulnerabilities.
Conclusion
Addressing the myriad vulnerabilities within the Internet of Things (IoT) landscape is essential for any organization aiming to leverage these technologies securely. This article underscores the critical need for CTOs to implement comprehensive security strategies that not only identify but actively mitigate IoT vulnerabilities. By prioritizing robust password policies, secure update mechanisms, and effective device management, organizations can significantly enhance their defenses against potential cyber threats.
Key insights discussed include:
- The importance of strong password practices
- The risks posed by insecure network services
- The necessity of maintaining up-to-date components
Furthermore, emphasizing user privacy and implementing secure data transfer protocols are vital steps in safeguarding sensitive information. The proactive measures outlined serve as a roadmap for organizations seeking to build a resilient IoT infrastructure that can withstand the evolving threat landscape.
Ultimately, the responsibility for securing IoT systems lies with every stakeholder involved. By fostering a culture of security awareness, prioritizing best practices, and continuously evaluating vulnerabilities, organizations can not only protect their assets but also instill trust among users. Embracing these strategies is not merely about compliance; it is about ensuring a secure and sustainable future in an increasingly interconnected world.